Saturday, December 15, 2012
Remove Hidden Data from MS Office Files
The Remove Hidden Data add-in is a tool that you can use to remove personal or hidden data that might not be immediately apparent when you view the document in your Microsoft Office application.
You can run the Remove Hidden Data add-in on individual files from within your Office XP or Office 2003 application. Or, you can run Remove Hidden Data on multiple files at once from the command line. In either case, to run the tool you must have the application installed in which the document was created.
To download the Microsoft tool to remove hidden data click here: Micorosft Tool
Saturday, December 1, 2012
Staying Up-To-Date with ColdFusion News
CFSpreadSheet: Real World Use
Tuesday, November 6, 2012
Spoofing from 'Apple'
 Domain Name: WELNESSMEDICAL.COM
Domain Name: WELNESSMEDICAL.COM Registrant:
Alulay Solorzano
Alulay Solorzano (campion@welnessmedical.com)
1105 Rowes Lane
Elizabethtown
KY,42701
US
Tel. +1.2706600129
Creation Date: 05-Nov-2012
Expiration Date: 05-Nov-2013
Domain servers in listed order:
ns1.welnessmedical.com
ns2.welnessmedical.com
Administrative Contact:
Alulay Solorzano
Alulay Solorzano (campion@welnessmedical.com)
1105 Rowes Lane
Elizabethtown
KY,42701
US
Tel. +1.2706600129
Technical Contact:
Alulay Solorzano
Alulay Solorzano (campion@welnessmedical.com)
1105 Rowes Lane
Elizabethtown
KY,42701
US
Tel. +1.2706600129
Billing Contact:
Alulay Solorzano
Alulay Solorzano (campion@welnessmedical.com)
1105 Rowes Lane
Elizabethtown
KY,42701
US
Tel. +1.2706600129
Saturday, November 3, 2012
Don't Forget About The Paper
 We are all getting computer security tips and tidbits from all directions.
We are all getting computer security tips and tidbits from all directions. So much so that sometimes we are forgetting about the simple stuff.
We all know that large databases need to be protected. We know to have a personal password policy and all that other stuff.
But sometimes we forget that the scraps of paper that float around our offices can be just as valuable to someone trying to obtain information they otherwise shouldn't have.
Don't forget about the printed reports you generate and pieces of mail that have been opened and you are just stepping away for a moment or to.
Keep information on paper away from prying eyes. Use a shredder when the information is no longer needed or you considered out of date for your personal use.
When you get to the office on Monday, look at your desk. What can you learn from what is around from just what you see.
Thursday, October 25, 2012
Got Spam? Don't Unsubscribe
At the bottom of all these messages is a nice enviting link telling you that if you do not wish to receive any more messages from whoever sent it just click.
Wait... DON'T DO IT.
When you do click to unsubscribe (as if you were subscribed) what you just did was tell the sender that in fact he / she does have a good address.
Now that verified good address will be added to other spam sender lists, even sold to yet even more companies who send unsolited email.
So just delete the message.
If too many of them are getting through take a moment and forward it to your email provider so they can take steps to add the sender to the spam filters.
Thursday, October 18, 2012
Do not allow your browser to store passwords for you
 Stored passwords allow anyone who can access your machine to log in to your web accounts as you. In addition, there are numerous utilities that can expose that hidden information and actually reveal the password. If you've reused that password for other logins, many systems or web sites could be compromised.
Stored passwords allow anyone who can access your machine to log in to your web accounts as you. In addition, there are numerous utilities that can expose that hidden information and actually reveal the password. If you've reused that password for other logins, many systems or web sites could be compromised. Saturday, October 6, 2012
Security Shortcut: Lock your workstation with one click
- Right click on an empty area of your desktop.
- Click 'New'
- Click 'Shortcut'
- Type the following:
- rundll32.exe user32.dll, LockWorkStation
- Click Next
- Name the shortcut; something like "Away From Desk"
- Click Finish
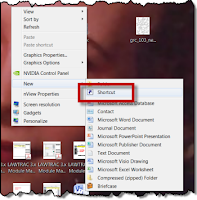 Now when you step away from your computer for a few minutes it is a quick double click and your computer is locked.
Now when you step away from your computer for a few minutes it is a quick double click and your computer is locked.Tuesday, August 21, 2012
Cybersecurity Becoming No. 1 Concern for GCs and Directors
Here is an interesting piece of information.
63% of the individuals surveyed by Law.com ‘s Corporate Counsel believe that the General Counsel needs to take charge of cybersecurity and not their IT departments.
Link: http://urtak.is/NJFOu1
Now this is going to come about through the Corporate Governance or Corporate Compliance areas of the corporate legal department. The skill sets that currently are located in the Information Technology departments will be absorbed by the GC. One group will be putting together the standards (governance) while the other (compliance) will be testing and checking.
Born from this will be additional national standards much like the ISO 9000 movement in the early ‘90s..
Tuesday, August 7, 2012
ColdFusion - List Functions
I thought I would pass on a little trick to those programmers who also have to design the data structures behind their applications.
If you plan on using table primary keys (usually a sequential number) as something to use in sub-queries or list structures consider starting you numbers at 1000 instead of 1.
Typically when creating a table I start the primary key with 1:
CREATE TABLE SomeTable (
TableID int NOT NULL PrimaryKey IDENTITY(1,1)
)
This works great except when you want to put the result set of returned values from a SQL statement in a string:
<CFSET SomeString = #ValueList(QueryName.TableID)#>
And then search that string for matching records:
#ListFind(SomeString, ‘3’, ‘,’)#
Sometimes you run into a situation where the first three (3) that is found is actually in a value like 103 or 33. The Find functions consider everything an alphanumeric and cannot restrict itself to numeric value only.
OK… here is the trick.
Start your numeric value in the primary key field with “1000” instead of “1”.
IDENTITY(1000,1)
If your data table is going to have thousands or hundreds of thousands then consider using an initial number even higher than 1000.
This will truly make your FIND operations run more smoothly and take the opportunity to mix up numbers every once a while.
Friday, July 27, 2012
URL for Sale
Tuesday, July 24, 2012
Apple Warms Up to Hackers, Plans Presentation at Black Hat
For years users of Apple computer products felt themselves protected against hackers and computer viruses. Seriously looking down their noses at PC users flaunting the bullet proof boxes as exhibit number one.
Yet, programmers then, and now, use the PC platform to be productive with. Windows based machines still dominate internet servers, programming platforms, database farms, individual productivity machines and more.
Why?
Because with Windows based machines we know what we have. We are aware of the obstacles that we have before us that we need to either over come outright or at the very least be aware of as we move along.
Now the age of hand held and tablet sized devices are ruling the end-user world. Heck, I have an iPhone, iPad and all those modern things too. But when it comes to being productive, writing applications for corporate America I still choose the Windows platform with keyboards I can bang away on and mice to point and double click with. We still need those things to be productive.
We opt for modern hybrid cars, but tolerate (understandably) eighteen wheelers to get the products we make and buy to market.
Anyway, back to Apple finally feeling the wrath of the rest of the world. Every PC professional on the planet knew this day was going to arrive. Apple, now that they are bigger than Microsoft and have more devices world-wide will become more and more of a target of those who need to prove their ability to bring others to their knees.
Yup, the tables are turning – targets are changing – and Apple users are now looking at us for assistance rather than distain.
Apple Warms Up to Hackers, Plans Presentation at Black Hat - Bloomberg
Saturday, July 7, 2012
Examples of Good Passwords
Tuesday, June 26, 2012
How Much Data Do You Have?
HOW MUCH DATA DO YOU HAVE?
CD = 650 MB = 50,000 pages.DLT Tape = 40/80 GB = 3 to 6 Million pages.
Super DLT Tape = 60/120 GB = 4 to 9 Million pages.
***************************
Page Estimates:
1 MB is about 75 pages;
1 GB is about 75,000 pages (pick-up truck full of documents).
Aver. pgs. per email: 1.5 (100,099 pages per GB).
Aver. pgs. per word document: 8 (64,782 pages per GB).
Aver. pgs. per spreadsheet: 50 (165,791 pages per GB).
Aver. pgs. per power point: 14 (17,552 pages per GB).
***************************
For the average .PST or .NSF Email File:
100 MB .PST file is 900 emails and 300 attachments.
400 MB .PST file is 3,500 emails and 1,200 attachments.
600 MB .PST file is 5,500 emails and 1,600 attachments.
A 1.00 GB .NSF file is 9,000 emails and 3,000 attachments.
A 1.5 GB .NSF file is 13,500 emails and 4,500 attachments.
***************************
Note: Many variables will affect ALL of the actual numbers above, including especially large image and video files, and recursive files.
***************************
Bits and Bytes Sizes:
•8 bits are equal to 1 byte (one or two words),
•1,024 bytes are equal to 1 kilobyte (KB).
•1,024 kilobytes (KB) are equal to 1 megabyte (MB or Meg).
•1,024 megabytes are equal to 1 gigabyte (GB or Gig) (truck full of paper).
•1,024 gigabytes are equal to 1 terabyte (TB) (50,000 trees of paper).
•1,024 terabytes are equal to 1 petabyte (PB) (250 Billion Pgs. of Text).
•1,024 petabytes are equal to 1 exabytes (EB) (1 000 000 000 000 000 000 bytes).
Friday, June 22, 2012
Go Daddy identified as spammer

The first thing that I hold against Go Daddy is the way they dupe people into registering a URL (web address). They will do it for you for a couple of bucks, but then THEY own it. It is your idea and your website, but they own the web address. Once they have it you can’t move it to a more secure environment or use one of the more dynamic programming languages because they own your ass.
Now they are allowing these spam pushers to register a quick URL and use their SMTP servers (send mail server) to process thousands (perhaps even hundreds of thousands) of spam emails. The spammers are doing this for only a couple of bucks.
Even their own Forums board (link below) is pleading with them to stop this practice of allowing so many spam email mills to use their servers to push JUNK.
Go Daddy identified as spammer | Forums | Groups | Go Daddy Support
Sunday, June 10, 2012
Cold War Soldiers Get No Credit - Here's Proof
 I don't wish to take anything away from the men and woman who server our country today, but I thought I would take a moment and let everyone know that those of us who served during the "Cold War" era get little if any respect.
I don't wish to take anything away from the men and woman who server our country today, but I thought I would take a moment and let everyone know that those of us who served during the "Cold War" era get little if any respect.A prime example below is a benefit for education benefits that are a loan of $1,000 that you have to pay back.
So it isn't a grant, just a help someone may want to use to get that additional certification or a little training to get a job or perhaps a promotion.
I qualify for the perk, but many I served with will not.
Lawmakers at the state and national level need to remember that the cold war era service men and women participated in the nuclear build-up in Europe, were held hostage in Iran, helped search for Pablo Escobar, stood guard at the DMZ in Korea, got shot at by the Red Guard in Germany, the list goes on and on.
Eligibility: Veteran must have served in the U.S. Armed Forces during one of the following periods: in Indochina between December 22, 1961 and May 7, 1975; served in the U.S. Armed Forces in the hostilities that occurred in the Persian Gulf from August 2, 1990, through September 10, 2001; served in the U.S. Armed Forces in the hostilities that occurred in the Persian Gulf from September 11, 2001, to the end of hostilities; served in the U.S. Armed Forces in the hostilities that occurred in Afghanistan from September 11, 2001, to the end of hostilities.
Lost cat, free puppy, yard sale, charity event
 |
| Each Pin Has A Story |
Wednesday, June 6, 2012
Failure to Restrict URL Access
| OWASP Logo |
The Open Web Application Security Project (OWASP) places something called "Failure to Restrict URL Access" as the ninth item on their list of the ten most prevalent security problems on the Internet today.
What is meant by the phrase is some web applications allow individuals to change the address in the web browser to access pages (or screens) they otherwise should not be allowed to see.
For example, if your dentist has a website where by you can go look up when your last appointment was and schedule a new appointment there should be a way for him (or her) or someone on their staff to go look who has set-up appointments or mark some days no appointment will be scheduled because the doctor will be out.
Those screens should only be accessible by the individuals who are employed by the dentist, and perhaps only a select few of those.
The OWASP rates this as something that offers a 'moderate' security rating. A security auditor may fail your application for corporate use altogether if this is allowed.
Even if these "administrator only" screens are password protected just finding the log-in screen by manipulating the URL it is cause for failure.
What can you do to manage this? Plenty.
First, make sure your application makes good use of session controls. As individuals are using your online application we don't necessarily need to know who they are, but that they are there and are using the application.
Next, make sure the only way the screen will display is if the viewer is coming from an authorized link. The very bottom of the main application screen may have "Site Admin Click Here". That link should carry some kind of dynamic variable (i.e. DayOfYear) that can be used to double check the referring URL and this dynamic variable. Both must be in place in order to see the admin log in.
One thing you may want to try is running your admin screens in a 100% IFRAME. If you do that then place the snippet below atop all your admin screens. If someone accesses the screen by changing their browser address directly to that screen they will be bumped back to the main application screen.
<script type='text/javascript'>
if(top==self)
this.location='../../default.htm'
</script>
So this is #9 of the OWSAP Top Ten list of security problems on the Internet. We can work together to get this moved off their list as begin to focus on other things.
Tuesday, June 5, 2012
For My Christian Friends
Monday, June 4, 2012
Picture Of The Day
Sunday, June 3, 2012
Sunday Walk
 |
| Call Box |
I took over 500 pictures, my theme (if there is such a thing) was 'everything'.
I made it to the parking lot of a local mall at around 8 a.m. I wanted to see what the advantage was from the top of the parking garage which is about four stories above ground.
While I was up there I was able to get some fantastic pictures of a hawk that was making his home behind one of the signs.
From up there too I got some pictures of a water tower with my zoom lense that makes it look like I had used a helicopter or something because I'm almost exactly even with the big green thing.
Everything was going great until mall security cornered me and kicked me off the mall's 'private' property.
Oh well....
 |
| Pink Rose |
Friday, June 1, 2012
Weekend Outlook
 |
| APIR |
Meetings shuffled, international customers who don't celebrate the US holiday of Memorial Day.
After playing catch-up and responding to the juggled agendas I'm looking forward to the weekend.
My plan was to get up tomorrow and play some more with my new camera. This time walking towards the nearby shopping mall called Rosevellt Field.
But the rain clouds have been gathering and 'they' (whoever they are) are calling for quite a bit of rain tonight through tomorrow morning.
Oh well, perhaps Sunday.
What do you have planned for the weekend?
Thursday, May 31, 2012
Digital Signatures - Value Added Taxes - Password Security
I know how lucky I am. Most people go to work and during their day they focus on a small set of projects or a distinct range of tasks. Which is great; people team up, do what they have to do and as a result they are productive.
In my position too I have a specific set of responsibilities, but in order to do them I have get to dive into areas of knowledge and educate myself in order to provide web application(s) that are more useful to those who need them.
For example, this morning I started by watching some refresher courses on Photoshop on Lynda.com with my morning coffee.
From there I had to brush-up on some regulation changes as they pertain to digital signature and how those changes might affect the application and our users (whitepaper to follow).
Following that I had to respond to some security concerns of one of our customers, and then I bounced to study the differences between the Value Added Tax laws between Canada, the Euopean Union in general and Italy.
And it's only 1 p.m.
I'll spend the afternoon writing code for the 4.0 release of our current software offering taking into account suggestions sent in from customers and the input from our advisory council.
I love the ability to challenge myself, learn about things I didn't know before and applying that knowledge into a tool that other use to do their range of projects and dedicated tasks. If I and my team do this right their projects will be a little less cumbersom and their tasks less 'tasking'.
Did I mention I loved my job?
Wednesday, May 30, 2012
Unfinished Fiber Optic Systems
I use to work for a company called SIECOR (now called Corning Cable Systems) out of their Hickory, NC location.
I worked for their field engineering division. After companies would buy the fiber optic cable we would follow along later and splice the cables together and put on the connectors once the cable was strung.
This was a great job, but a lot of work and even more travel. We did jobs that took months to complete in Ohio, California, New York, all over. These were networks for intelligent traffic systems, cable TV networks, even college campuses like UC Davis.
I must say that here around Long Island, NY there is way too many of the situations in the image above where the minimum number of splices were made to do the local ‘drop’ (terminate a fiber or two) and the excess cable is just rolled and left to the elements.
With regards to the technology, there is nothing wrong with this. These cable systems need lots of excess to counter cables that break or to expand on the capabilities of the network at a later date. But there are better ways of doing this.
Notice the little loop mechanism next to the large loop of loose cable. We called these ‘snowshoes’ and is an excepted way to hang the excess cable slack. You slide the two ends closer together and you’ll get the slack you need.
The large loop is susceptible to excess weight during snowfalls, ice will form creating an additional hazard; it is just unprofessional and quite frankly irresponsible for the company who put in this network.
I sure hope that over the summer I’ll be able to see all these loops of slack cleaned up in some way.
Tuesday, May 29, 2012
Early Morning Yesterday
 |
| Memorial Day 2012 |
The sun was pushing back the clouds that had covered our town for the past three or four days. It was up far enough to lighten the sky, but not so far as to turn off the lamps.
The streets are still quite.
Monday; only a few would be stiring today, after all - it is a holiday.
Memorial Day.
In just a little while there will be marching bands and boy scouts, little league teams and the woman's auxaliary all participating in making some noise.
But for now; for this moment of dawn it's quite.
Time for me to remember Vincent and Shawn; Robert (Bobby) and Paul; and all those others.
 |
| Memorial Day 2012 |
Modern Shotgun Wedding - True Story
Denial-of-Service Attacks

This seems to alarm a lot of people; so I thought I would take a moment and explain what the most common of these attacks are and how they effect you.
The most pervasive “attack” is called “Denial-of-Service”. This is where someone writes a little program that asks a website to do something over and over again, as such speed that it does not have time to respond to other legitimate requests.
We’ve all been there; in a restaurant waiting on our server to stop by, but he or she is too caught-up with another customer who is monopolizing the server’s time so they can’t respond to the other customers in their area.
This customer who is being the jerk is denying you of service.
This happens mostly to those online services offered by government agencies who have to open their web application up to the general public, so you see this a lot with the IRS, Medicare, things like that.
The entities executing such attacks are not looking to steal any of your information, they are just trying to make a political or social statement.
So if you see this in the news don’t be too overly alarmed.
There are some of these attacks done against free service email addresses and alike, those too are more a pest than a problem. I’ll discuss those in a later post.
For more information about denial-of-service attacks click the link below.
US-CERT Tip ST04-015 - Understanding Denial-of-Service Attacks
Sunday, May 27, 2012
Device may inject a variety of drugs without using needles
The military has been using air injectors since I went to basic training back in 1981. We would roll up both of our sleeves and stand in a line. As we moved forward there were individuals standing on both sides of us with these air injectors.
Some guys flinched, when they did the air gun would shoot their load and cut open the guy’s arm.
To this day I have pits on both sides of my shoulders where I got those shots.
These guys from MIT haven’t come up with anything new. In fact they have invented a way to better transmit bacteria from one person to another.
Health Warning: CLICK HERE
The full story from the MIT website is linked below.
 |
| Time For Shots |
Device may inject a variety of drugs without using needles - MIT News Office
Is Facebook going to buy Opera, make its own browser?
This story that appeared on the Internet over the weekend on sites like The LA Times (link below) and others concerns me.
To date – the programmers of Facebook have not invented anything. What they are really good at is taking established technologies (php, sql, jquery) and applying them to an application.
Like a painter of landscapes. They take tubes of oil paint and apply them to a blank canvas to create a wonderful, inspiring picture.
The painter of the wonderful scene did not weave the canvas, stretch it over a frame they made, applied paints they created with brushes they crafted. And that’s fine, the final product is what is important.
If Facebook is to buy Opera they are going to have to dive deeper into the nuts-n-bolts of actual programming. They will more closely have to pay attention to the standards of W3, operating systems, guidelines of OWASP and more.
I’m not saying that they can’t do it, I am saying that it isn’t a match to their core capabilities they have demonstrated thus far.
It will be interesting to see how this unfolds.
Is Facebook going to buy Opera, make its own browser? - latimes.com
Friday, May 25, 2012
US hackers take cyber war to al-Qaeda sites

This news was released during a press conference by none other than our Secretary of State; the person who we will be turning to to perhaps conduct peace negations if the opportunity arises.
Even if the US is going to take on the tactics of hacking enemy web sites to sway public opinion or to perform some kind of counter intelligence this function it should be done by members of the US military, perhaps the Signal Corps who employ a special operations section just for this purpose. (as was the case here)
Never should our State Department engage in activities other than those with peaceful intentions.
I understand and support actions against those who wish to put my head on a stick, but there needs to be some kind of separation between conducting war and obtaining peace.
What You Look'n At?
 |
| What You Look'n At? |
Still, she was uneasy.
Thursday, May 24, 2012
Legal Considerations - Social Media
Tuesday, May 22, 2012
Really Bad Picture Needs a Caption
By all rights this photo is bad... beyond "soft".
I'm thinking "Digging For Home"... what caption would you put on it?
 |
| Digging For Home |
Hackers Could Impersonate You – Here Is Proof
Here is a real-world example of how individuals can call a service provider and pretend they are you in order to gain access to home, accounts and more.
In this case a person called the hosting service for a web application the processed credit card payments and pretended to be the owner. The service accepted the verbal request to change the account credentials so the imposter could access the source code and database.
How does this apply to your life?
- Could I call your bank and pretend I am you?
- How about your home alarm service?
All I would need to know are simple things about you. Your name, date of birth, zip code; things I could find out very easily.
The burden is on the service provider. Do they allow telephonic inquiries about your account? Can I add account users over the phone?
While this event happened to a company – the principal could be applied to any one of us.
Monday, May 21, 2012
Anonymous Leaks Data & People Loose Perspective

Some hacker got through to a US Department of Justice server that did nothing more than collect statistical data on the visitors to the site.
Information like what website referred them, their general geographical location, screen size; things that all websites collect so they can better understand their audience.
But because this was a US Department of Justice server the individuals who decide what the news is thought they would generate a few more readers if they clanged a few diner pots together and tapped into the fears of individuals who don’t understand computers and the Internet.
After all, what kind of damage is 1.7 GB of visitor information to a web site going to really provide someone? The average screen size or type of web browsers they had?
On the pretibial scale of 1 – 10 this information leak is a 1. But it makes for a provocative headline; don’t fall for it.
Anonymous hacks Bureau of Justice, leaks 1.7GB of data | ZDNet
Memorial Day 2012; Where Is Your Focus?
This experience gives me an appreciation for those who went before me and those who followed who gave their life to preserve the freedoms I have.
As we move towards this holiday weekend I would ask everyone to take a few moments and adjust their focus from the holiday aspect to the intent of the day which is to honor the men and women who have died to preserve freedom.
It is nice that communities set-up a statue and put names of these heros on a wall, but how often do we look at the statues and not the names?
Take a moment and adjust your focus. Incorporate a few of the names into your moments of reflection.
Sunday, May 20, 2012
Hawk
Took this with a 300x zoom, wasn't sure how it would turn out.
Cut it down - I think it would make a nice background for the top banner on a website. If you need something that is wider than this let me know.
Saturday, May 19, 2012
IAVA - CNN: Paul Rieckhoff
Once again CNN has turned to Paul Rieckhoff of Iraq and Afghanistan Veterans of America (IAVA) as expert in the field of military experience.
Here is a quote from the current interview about National Guard soldiers returning and looking for employment:
“Before 9-11 National Guard units almost never deployed, didn’t go to combat, and for the most part you had one weekend a month and two weeks in the year. Now you have National Guard units which have been deployed three times for a year. They’re not weekend warriors, they are full-time warriors now.”
I believe Mr. Rieckhoff needs to look at the number of soldiers who were deployed during the Korean and Viet Nam conflicts and research what happened to the National Guard units in the 1940’s before he sells veterans of his father’s and grandfather’s era.
If you are going to speak with authority on a subject better know that subject. The soldiers who server in the National Guard need assistance in finding employment; this I agree with.
Don’t miss quote history in order to make yourself sound more important.
I have a number of other issues with IAVA, this Rieckhoff fella is number one on the list.
One Man Boat Race
I had always been intrested in the hobby. For a short period of time I was an Army Journalist (71Q) and then worked for the Taylorsville Times for a couple of years where we had to take and develop the photos for the stories Lee Sharpe sent us out to cover.
I wanted something of intrest to take pictures of so I go onto the Internet to the Eisenhour Park calendar of events and saw that the model boat club was going to have a race.
I thought great, fathers with sons, model boats, a nice spring morning. Should prove to be a nice subject to play around with exposure times, shutter speed, all those things I had viewed on the instructional videos.
At dawn I start headed toward the park. I wanted to get the sun rising and actually got a few neat shots with the beams of the early morning light reflecting off train tracks, burning the dew off the grass on a golf course and some others I'll post later.
But the boat race was a bit dissapointing.
Only one guy showed up. So I guess at the end of the day I got pictures of the winning boat.
Tuesday, May 15, 2012
You gotta be kidding me.....
Fake money....
This is a service where people purchase 'coins' that are used to trade for other goods and services. A fake economy.
According to the WhoIs search from Network Solutions this attempt to corner the internet economy is one K.K. Tibanne of Shibuya (Toyko) Japan.
Along with the fake coinage user's names, emails and trade history were taken. According to Computer World the passwords were all encrypted, but it said nothing about the credit card accounts of those who had purchased the online trading money.
Not-for-Nutt'n; sorry the user's information was taken, but I'm not getting too excited over this. If their application security was this bad it is a good thing they were taken down.
 |
| Computer World Story |
Friday, May 4, 2012
LifeLock - Government Sanctioned Rackateering
I really think with the comericials they are really playing on individuals fears, which I hate more than any other sales tactic.
Refrence on other information: Click Here
Consider for a moment the small print that appears on the bottom of the screen during their comercial. No commentary here, judge for yourself....
- No one can prevent all identity theft
- Checking and savings account takeover alerts require LifeLock Ultimate membership
- Network does not cover all transactions and scope may vary
- No one can prevent all identity theft
- Guarantee applies only if you become an ID theft victim because of a failure in our identity theft service. Restrictions apply. See LifeLock.com for details. Due to New York State law restrictions this LifeLock service guarantee cannot be offered to residents of New York.
Wednesday, April 25, 2012
Sunday, April 22, 2012
BS Alert
 So I'm hanging with friends on Saturday and a guy who was known to some in the group but not to myself join and started talking... and talking... and talking.
So I'm hanging with friends on Saturday and a guy who was known to some in the group but not to myself join and started talking... and talking... and talking.The level of BS this guy was spreading was so accute that I had to check to see if I had boots on to protect my feet.
One layer of the crap was a story about a friend of his, who was married with three kids, joined the army after 9-11. The guy was thirty-eaight years old when he joined and turned forty in basic training.
First of all, the cut-off age for joining the military is 35. Second, you can't be a private in the army if you are married with three kids (the max is two, they do this for economic reasons). Finally, the guy would not have spent two years in basic training.
Anyway, that was just one part of my weekend.....
Tuesday, March 13, 2012
KFC 70 Charger R/T–Commercial
Anyone else notice how dirty the dashboard is?
Hard to believe anyone who cares for a car that looks this good would have such a dirty dashboard.
The Sergeant who Killed Civilians
I was once a solider. Served my country on every continent on the planet except Australia.
The act of one who followed in my and other’s footsteps to serve in the forces which protect this country and it’s way of life saddens me.
Let’s take a look at what should now happen.
We have no Status of Forces agreement with Afghanistan. Those are treaties with countries where US service members serve.
For example, in Germany, if a soldier gets a speeding ticket then he or she has to pay the ticket to the governing German agency. If they were to rob a bank, the status of forces agreement allows the United States to take custody of the individual and they face courts governed by the United States. Everything is spelled out in the treaty.
If we had a situation where an Afghan soldier were stationed at Fort Bliss, TX and he ran amuck killing US citizens we would want to process the individual according to US law.
To save lives from retaliation for what this “sergeant” did we must hand the person over to Afghanistan TODAY so he can face the consequences for his actions.
No it isn’t fair when you consider what we believe is fair and just; and you know what is going to happen to this guy.
We have to do this.
If we are the ones who believe in the order of law and justice then let us show the world that we respect local laws and international treaties.
Status of forces agreement - Wikipedia, the free encyclopedia
















